Industrial Grade Linux
Now it's real(ly) time!
Industrial Grade Linux
Now it's real(ly) time!

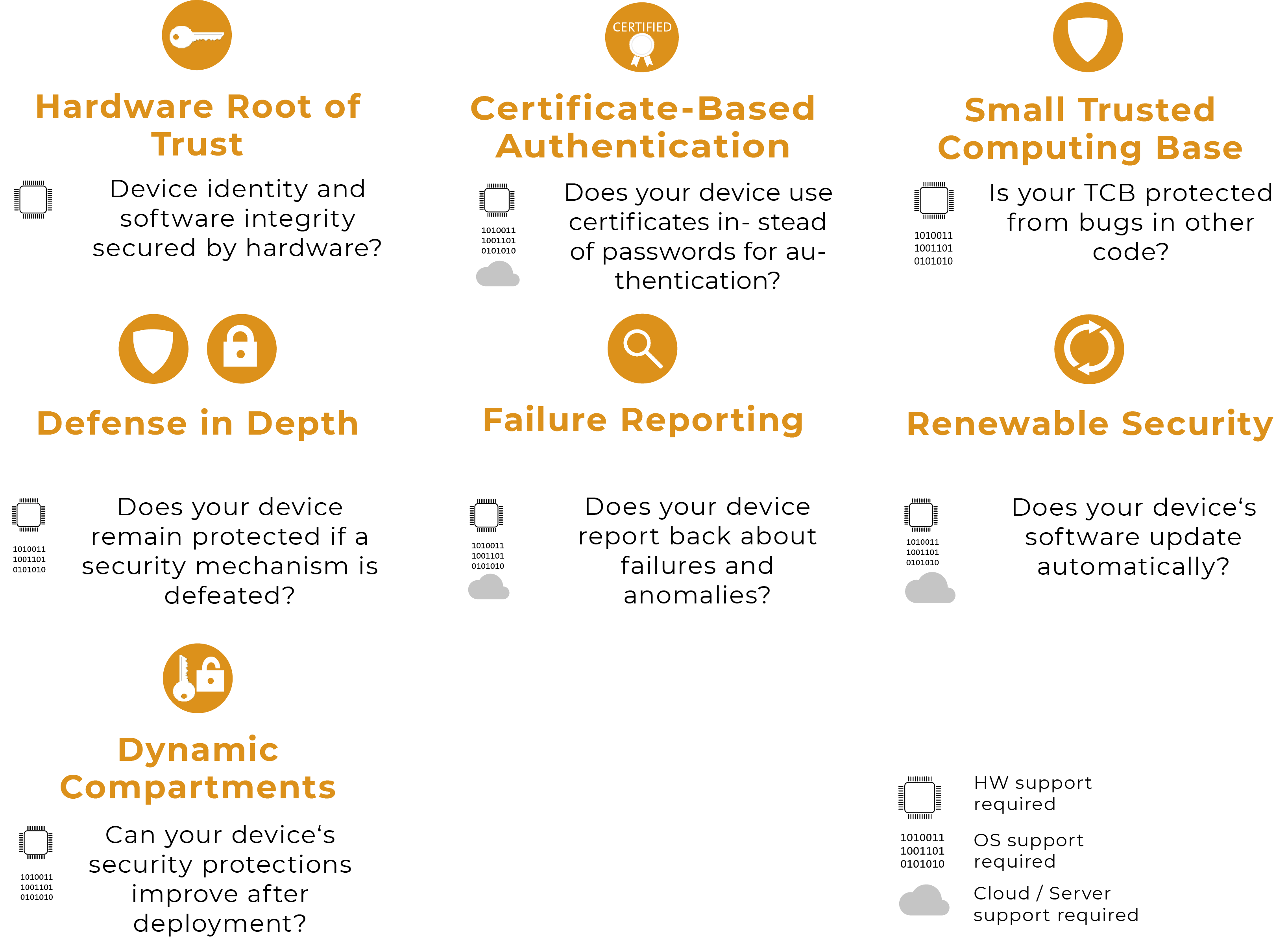
The principal requirements for a secure (embedded) system and their implementation (without claim to completeness):
Trust in an embedded product is more important than ever in times of networked devices. People expect a system to work according to plan. Applications trust that the operating system works correctly and does not falsify data. Servers in the cloud rely on the identity of connected devices being correct.
Unfortunately, the recent past has shown that embedded devices have often been used as a gateway for malware or for targeted attacks on infrastructure. Outdated software, the lack of secure updates and the longevity and frequency of these devices make them a prime target for attack.
Devices in the industrial internet (IIoT, Industry 4.0) must therefore be "secure" and generate trust. To this end, they should, if possible, meet the following security requirements:
|
A) Hardware b) Software c) Device management |
Whether all these requirements have to be implemented or how they should be implemented, depends on the definition of the safety level of each individual device. You should also bear in mind that more and more requirements are being imposed by legal and regulatory authorities.