Industrial linux
Now it's real(ly) time!

Industrial linux
Now it's real(ly) time!

Also known as ZTO – Zero Touch Onboarding
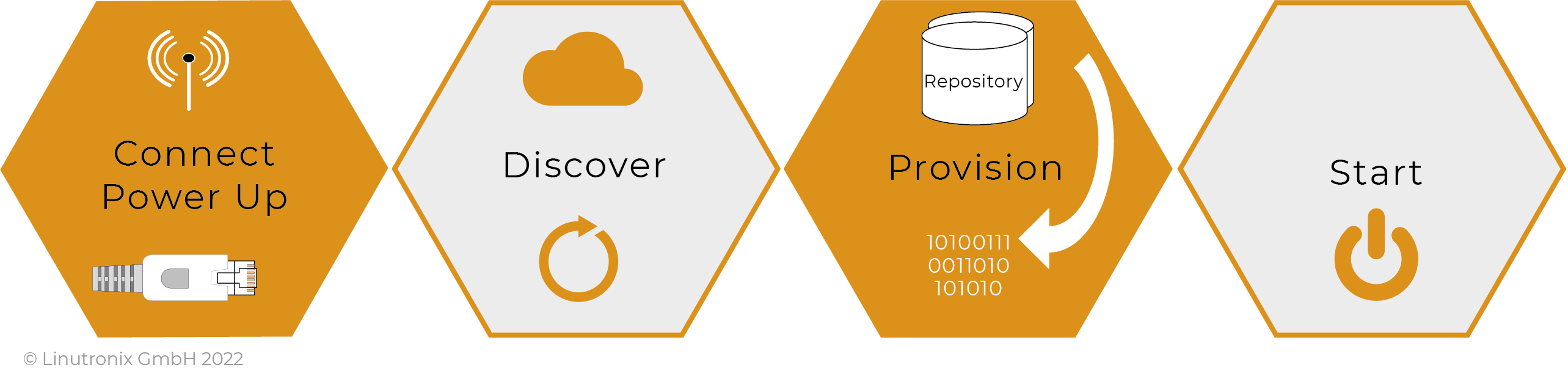
The IIoT (Industrial Internet of Things) raises serious new security challenges that become more acute as the scope and scale of IIoT systems increases. IIoT devices are often equipped with outdated software at the time of commissioning, so they require an update. And, according to their task, they must connect to a server (cloud) to exchange data. To do this, the devices must be uniquely identifiable and able to connect to a dedicated server.
| For security reasons, the connection between the server and the IIoT may only be established after both parties have been able to authenticate themselves unambiguously. |
One solution hereto is Secure Device Onboarding, also called Zero-Touch-Onboarding. This allows IoT devices to be configured with settings that are stored in a central server. As soon as a device becomes active, it connects to this server and its configuration settings are automatically installed with no need for a technician to intervene. This allows operators a much faster onboarding method while minimising the attack surface on the devices.
| Regardless of the ZTO method chosen, except for the SDO method (see below), an exchange of information between production and server-based registration is always necessary. |
A secure connection to the (cloud) server requires the IIoT device to authenticate to the cloud backend. This may be based on various procedures:
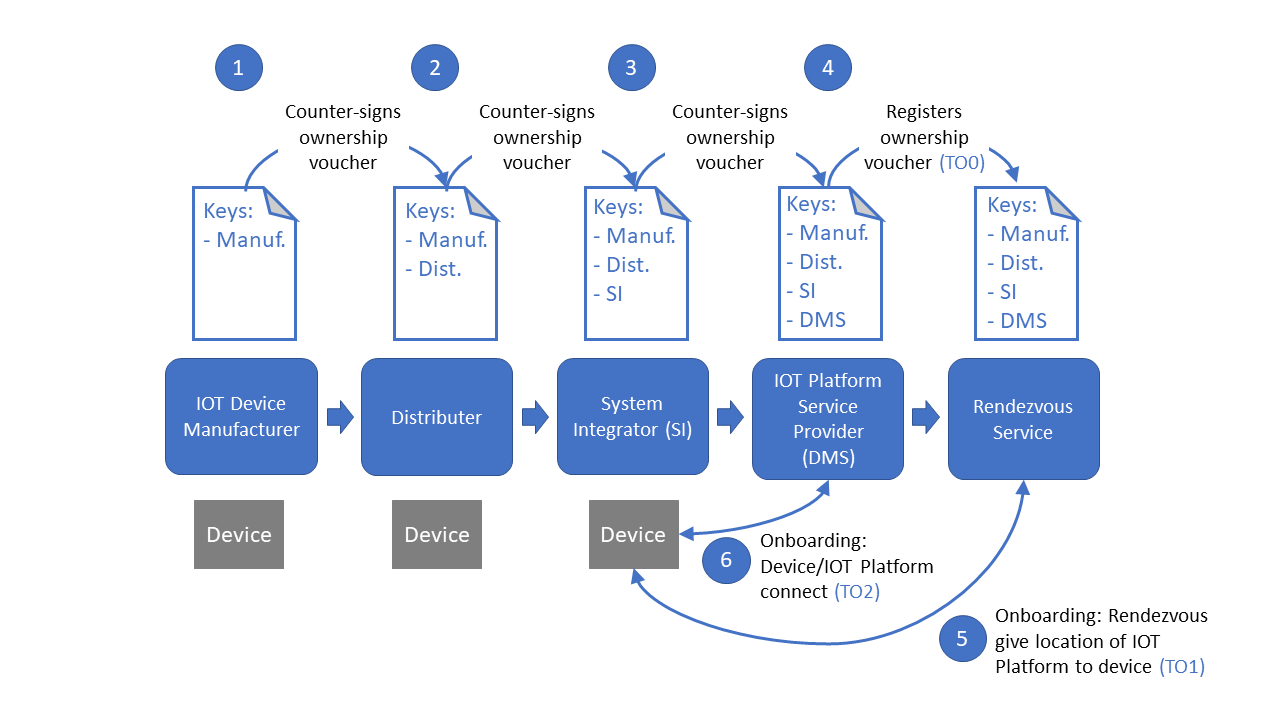
All these solutions have in common that they allow a unique assignment of devices that can be traced back to the current user. This is where the Secure Device On-Board process comes in, which was originally developed by Intel under the name EPID (Enhanced Privacy ID). Since February 2020, this solution has been open source and is hosted by the Linux Foundation4. The onboarding here must run via a dedicated Rendezvous server, the code for which was also provided by Intel.
The advantage of this approach, apart from the improved protection of privacy, is the fact that the target platform (cloud server) need not be known at the time of production.
The key benefits of Secure Device Onboard are:
The following picture gives an overview of the trust chain in this SDO procedure:
We would be happy to work with you to find the right solution for your use case.
1 Firmware TPM, mostly consists of Trusted Zone (TZ) and a dedicated memory, which often is an eMMC with a replay protected memory block (RPMB)
2 TCG TPM v2.0 Provisioning Guidance, https://trustedcomputinggroup.org/resource/tcg-tpm-v2-0-provisioning-guidance/
3 https://azure.microsoft.com/de-de/resources/azure-sphere-device-authentication-and-attestation-service/
4 https://www.lfedge.org/projects/securedeviceonboard/
https://secure-device-onboard.github.io/docs/latest/